The technologies, tools, and methods used to capture, manage, store, preserve, and deliver content across an enterprise.
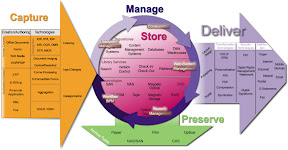
Unstructured data or -information refers to masses of computerized information, which do not have a data structure, which is easily readable by a machine. The most important item to remember is that content is vital to an organization. Ultimately, the greatest value is ensuring proper management techniques and tools are available, understood and proper integration. My opinion is that no one single function is greater or lessor than any other component within the model, all components are relative at a peer level and without this view a incomplete model exists and will not operate successfully. I will not decompose the functional framework; a granular level for each function has an operational view that creates an interdependence crossing each function. Understanding the core components of a ECM environment provides the baseline for defining vision and direction for the business. The five (5) core modules are: Capture - comprises how business content, whether paper or electronic, is transported into a content repository for reuse, distribution, and storage; Manage - comprised of tools and techniques for moving content around an organization and monitoring those tools’ performance; Store - determines where the content goes and how it can be located; Preserve - for long-term archival and storage of organizations' essential content resides; Deliver - determines how to get the right content to the right audience on the correct device.
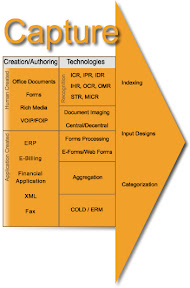
The Capture Model comprises how business content, whether paper or electronic, is transported into a content repository for reuse, distribution, and storage. The Capture Module contains functionalities and components for generating, capturing, preparing and processing analog and electronic information. There are several levels and technologies, from simple information capture to complex information preparation using automatic classification. Capture components are often also called Input components. Manual capture can involve all forms of information, from paper documents to electronic office documents, e-mails, forms, multimedia objects, digitized speech and video, and microfilm. Automatic or semi-automatic capture can use EDI or eXtensible Markup Language (XML) documents, business and ERP applications or existing specialist application systems as sources. The first step in managing content is getting it into the IT infrastructure. While internal company documents are born, and remain, digital throughout their lifecycle organizations still needs to ingest a tremendous amount of paper-based communications from outside. Checks, invoices, application forms, customer letters, etc., all need to be turned into digital form for insertion into the content management electronic workflow and/or directly into storage. Capturing documents puts them in motion and enables the information contained in those documents to be acted upon. While Citiroup predominantly refer to capture as the digitizing of paper documents, capture can also mean ingesting electronic files into your content management environment.
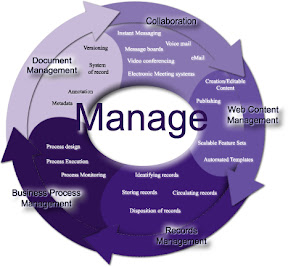
The Manage Module, comprised of tools and techniques for moving content around an organization and monitoring those tools’ performance. The Manage Module is for the management, processing, and use of information. A closed ECM system is to provide manage components just once as services for any “Manage” solutions such as Document Management, Collaboration, Web Content Management, Records Management and Business Process Management/Workflow. To link the various “Manage” components, they will have standardized interfaces and secure transaction processes for inter-component communication. Solution must be a component of, and include a complete and integrated product suite at the module level as defined. This module has an initial scope of the following sub-categories and will have addition as the document develops. Security requirements; to ensure the technology supports secure access that meets organizations business needs, the solution must also be assessed with respect to how it supports end-to-end security as related to user authentication, document authentication, and secure network transactions over the Internet, Intranet, and Extranet as necessary. The complexity and scope of organizations security issues especially when dealing with distribution will require the collaboration of multiple sectors, segments and lines of business organizational disciplines including legal, business operations, system administration, network administration, vendors, and external users of the system. For more information on security related requirements, organizations should review for consideration, ISO 17799 Information technology -- Security techniques -- Code of practice for information security management.
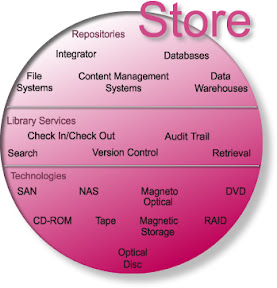
The Store Module determines where the content goes and how it can be located. The Store Module is used for the temporary or transient storage of information, which it is not required or desired to archive. Even if it uses media that are suitable for long-term archiving, “Store” is still separate from “Preserve.” These infrastructure components are sometimes held at the operating system level like the file system, and also include security technologies, which will be discussed farther below in the “Deliver Module” area. However, security technologies including access control are super-ordinate components of an ECM solution.

The Preserve Module addresses long-term archival and storage of organizations' essential content resides. The Preserve Module of ECM handles the long-term, safe storage and backup of static, unchanging information, as well as temporary storage of information that it is not desired or required to archive. For purely securing information microfilm is still viable, and is now offered in hybrid systems with electronic media and database-supported access. The decisive factor for all long-term storage systems is the timely planning and regular performance of migrations, in order to keep information available in the changing technical landscape. This ongoing policy is called Continuous Migration. The Preserve Module contains special viewers, conversion and migration tools, and long term storage media.
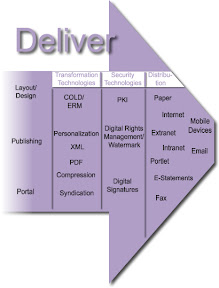
The Deliver module determines how to get the right content to the right audience on the correct device. The deliver module for ECM is used to present information from manage, store and preserve modules. They also contain functions used to enter information in systems (such as information transfer to media or generation of formatted output files) or for readying (for example converting or compressing) information for the store and preserve components. The functionality in the deliver module is also known as “output” and summarized under the term “Output Management.” The deliver module comprises of three groups for functions and media: Transformation Technologies, Security Technologies, and Distribution. Transformation and Security as services belong on the middleware level and should be available to all ECM components equally.
2 comments:
Interesting position and prespective how is the best way to get/gain acceptance in a company model?
With today's emerging focus on cradle to cradle engineering, based on mistakes of the past, I suggest you add somethign like a "Dispose" "Destroy" or "Delete" module. Having a destruction strategy for ESI (or a standard module that assists with the various types of destruction needed depending on what content you are dealing with) will help vendors help organizations avoid one of the single biggest problems facing ILM today - the extreme proliferation of too much information that is no longer useful, is expensive to maintain (much more than just the storage cost), and often is a serious legal liability.
Its not part of the "traditional" ECM modules but is long overdue to be added.
Post a Comment